- Create & Manage Cases in an Efficient Way via Case Management Option
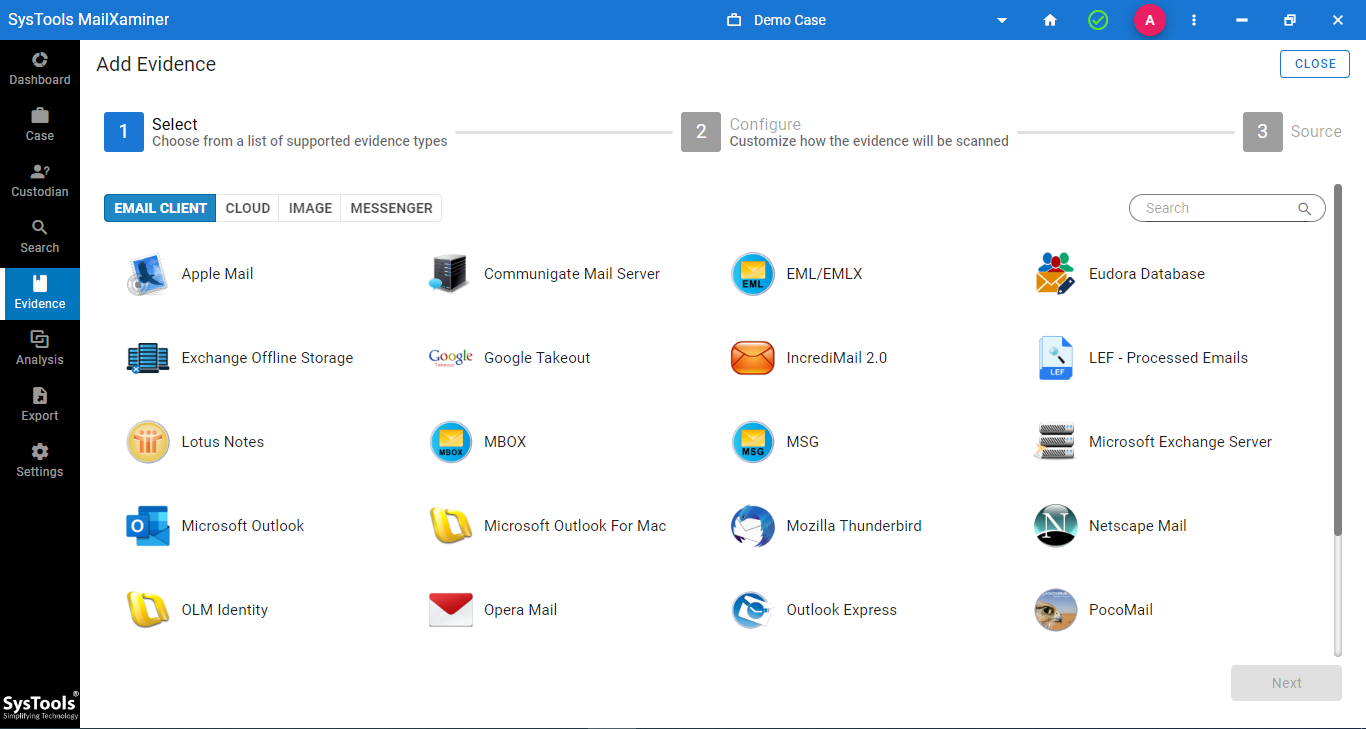
- Supports 80+ Email Platforms of Both Desktop-Based or Web-Based Email Clients
- Supported Desktop Email Clients - Microsoft Outlook, Thunderbird, Lotus Notes, etc.
- Cloud-Based Platforms - Office 365, Gmail, G Suite, Live Exchange, IMAP, etc.
- Compatible with Disk Drive Image Files - DD, DMG, E01, LEF, and ZIP
- Comes with Multiple Mail Views - Mail, Attachment, Message Header, MIME, RTF, etc.
- Examine Skype Messaging Application Database Details Such as Chat, SMS, Calls
- Advanced Link Analysis to Track Direct and Indirect Conversation of the Users
- Multiple Keyword Search Types - General, Fuzzy, Wildcard, Proximity, Stem
- Use Search Operators to Apply Conditions to Filter Out Desired Evidence
- Language Support for Search in Japanese, Chinese, Korean, French, Spanish
- Save Evidence in Court Acceptable Format by Recovering Deleted Email Components
- Generate Export Report with All The Detailed Information in CSV and PDF
Download Now
Safe & Secure